30 Oct Protect your computer against Cryptolocker Viruses coming by attachments
When receiving an email attachment:
– Do NOT open an attachment if you don’t know what it is.
– Use caution when opening attachments that you weren’t expecting or that you don’t know the content. Computer viruses are sent via e-mail attachments and can compromise your computer, data, financial and personal information.
– When an email attachment has a file extension ends with .zip, .exe, .com, or vbs. 99.9% of the time is viruses, Trojans, malware or spyware.
File Extension examples:
When you see attachment, most of the times you can see an icon on the attachment that will give you an idea what the file is. However, if the file doesn’t have an icon because the file is compressed or the program to open the file is not
installed on your computer.
Another way to identify what the file is about is by looking its file extension.
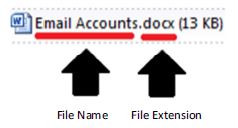
File Name File Extension
Word Document: .doc or docx
Word Perfect: .wp
PDF (Adobe): .pdf
Microsoft Excel: .xls or .xlsx
Microsoft Power: .ppt or .pps
Music: .mp3, .wav, .wma , .aac
Video: .mp4 , .avi , mpeg , .wmv,
Pictures: .jpg , .jpeg , .bmp , .tiff , .png or .gif
If you can see the file extension on your computer files or Outlook, call Telx.
Severely infected computers send viruses to other users across the network by using contact list of your email software and shared resources within your office.
– By mentioning this, you might receive an attachment from one of your known contacts; however, these attachments could be infected since their computers are infected on their end. If you open these attachments the likely scenario is that your computer will get infected and your contacts will receive an email that you did not send including infected file as an attachment. If you see a behavior you can notify the sender that their computer is infected or delete the email.
Understanding ZIP Files:
– Zip files are compressed files. The purpose to sending/receiving Zip files is to make attachment size smaller or send multiple files into 1 compressed file.
– Most of compressed files contain files that could be a virus. This is a way that the attacker bypasses the virus/spam protection.
Other Things to consider:
– Shipping companies like UPS, DHL, Fedex, or USPS won’t send you any attachments, all transaction are done through their website. If you are not sure call the shipping company.
– Bank institutions won’t send you links or attachments regarding your statements or wire transfers. You can only check this information on your Online banking by using the bank website.
– If you are not sure whether to open the attachment call Telx to verify if this attachment is not infected.
Email Scams:
– Your bank institution won’t send you an email requesting information or attachments (unless it is a banker from your branch or something you were expecting), statements, requesting to re-enter about your personal information or a wire transfer via email, unless you have alerts setup. The purpose of those emails is to obtain account information from the users.
– Whenever you open a link on these emails, they copy the design of the website making it look legit and the user enters information about their account, next day you will find out the account has been compromised.
– IRS/Equifax/Transunion/ won’t request any information via email, if they do most likely will be via regular mail. Dismiss these emails and don’t open these links.
– Whenever you win or got something for free over an email, the only thing that you can win is a big problem. Delete these emails immediately.
Virus Scams:
– If the FBI, NSA, Department of Homeland Security, or CIA has blocked your computer with a pop-up, these are signs of infections. These pop ups are to cheat users to gain financial information.
– Fake Antivirus protections and optimizers can pop-up during an infection not allowing you to work peacefully.
– These viruses request users to enter credit card information or do a transfer to an account to release their computers, please report these issues immediately.
How to avoid these issues:
– Understanding email attachments.
– Have an updated operating system.
– Have an updated Antivirus protection.
– Have an up-to-date network firewall and gateway security to prevent future attacks.
– Scan your attachments on this website: www.virustotal.com (this will scan your attachment with 60 different antiviruses in seconds). To do so, save the attachment without opening it and upload the file into the website.
– Call Telx if you have any questions regarding an email attachment.